
This post details my experiences getting the GNS3 VM on ESXi to work with 802.1q. I’ve been using the GNS3 VM on VMware Workstation for years, so far I’ve been unable to get virtual devices on the GNS3 VM to link to external networks using 802.1q. From my research I believed the issue to be due to the network interface card / drivers not supporting / stripping the 802.1q vlan tags. Recently I needed this work so I thought I’d give it a go running the GNS3 VM on ESXi. As long as your using VMware compatible network adapters 802.1q works fine with ESXi.
When researching how to present multiple vlans to the GNS3 VM, I discovered some people use a vmnic per vlan. That approach doesn’t scale well, especially if your trying to emulate a complex topology with many vlans.
Enabling 802.1q on the GNS3 VM
First install vlans on the GNS3 VM:
sudo apt-get install vlan
Load 802.1q into the kernel:
sudo modprobe 8021q
To load it permanently so it survives reloads of the VM:
sudo su -c 'echo "8021q" >> /etc/modules'
Adding a VLAN to GNS3 VM for management
You could use another vmnic to handle your 802.1q connections but I prefer to use a single vmnic where possible. A single vmnic was assigned to each GNS3 VM for both management of the VM and for 802.1q traffic to the VMware vSwitch. This approach requires a vlan be created on the VM at the host level in the below example the interfaces file on GNS3 VM was modified to create a vlan 31:
sudo nano /etc/network/interfaces
auto eth0.31
iface eth0.31 inet static
address 10.93.31.8
netmask 255.255.255.0
gateway 10.93.31.1
dns-nameservers 10.93.30.2 10.93.30.3
vlan-raw-device eth0
Please note, you’ll need to keep a record of your interface configuration as when you update the GNS3 VM the networking is overwritten.
I’m hopeful that one day the GNS3 team will prevent the networking configuration from being overwritten during upgrades. With many VM’s this could become annoying each time you upgrade GNS3 you need to reconfigure the networking settings on each VM 🙁
You only need to configure a vlan at the host level for management of the VM. There is no need to add vlan’s that you intend to use with the cloud link as tagged frames passed from the GNS3 cloud to the host’s Ethernet port will be forwarded to the VMware vSwitch, as long as 8021q is enabled on the kernel detailed earlier in this post. You will also need to ensure the port group is configured to permit all vlan’s. This is achieved by setting the VLAN ID to “All (4095)”
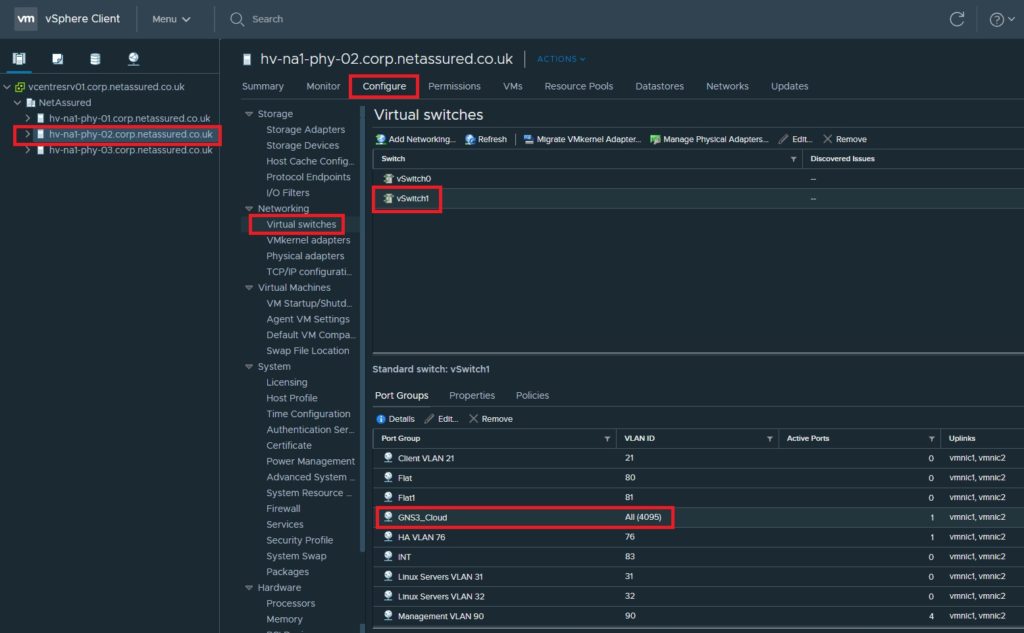
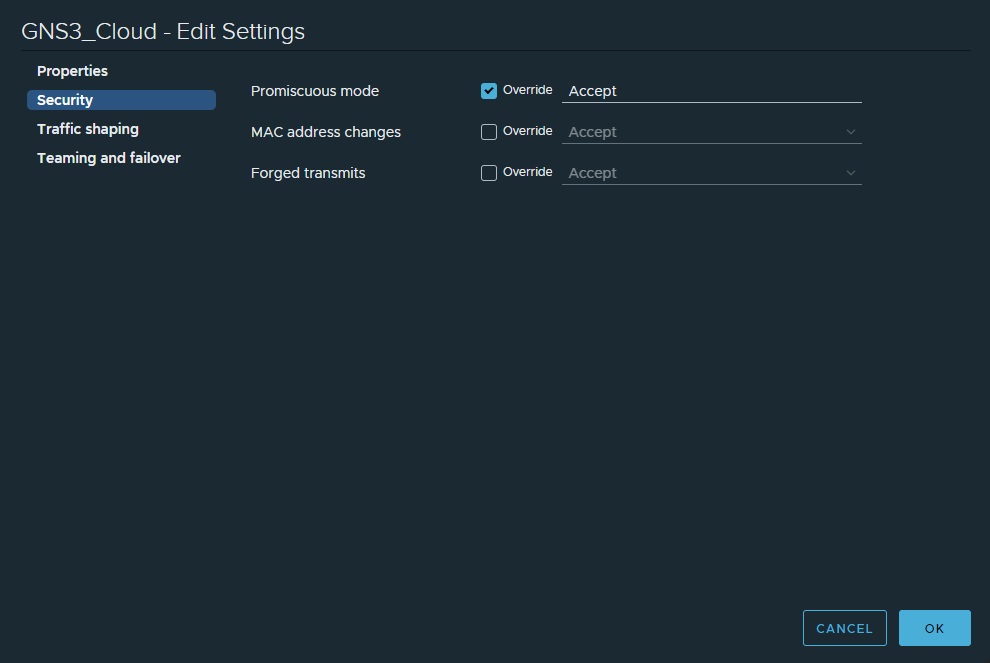
Enabling Promiscuous mode on the port group
You must ensure promiscious mode is enabled on the port group you’ve assigned to the vmnic on the GNS3 VM. This bypasses security to enable frames with mac addresses not assigned to the vmnic (your GNS3 devices will have different mac addresses). Edit the port group and enable as below:
Connecting a device on the GNS3 VM to external network
When connecting a device on the GNS3 VM to the external network use a GNS3 Cloud. Connect an Interface on the device to the ethernet port on the GNS3 VM. Connect it straight up to the actual ethernet port, not the VLAN interface. In my case its eth0. From the image below you can see I’m running 2 GNS3 VMS’s and each one has its own cloud connecting to the vSwitch on its respective ESXi host, mine are named HV01 and HV02: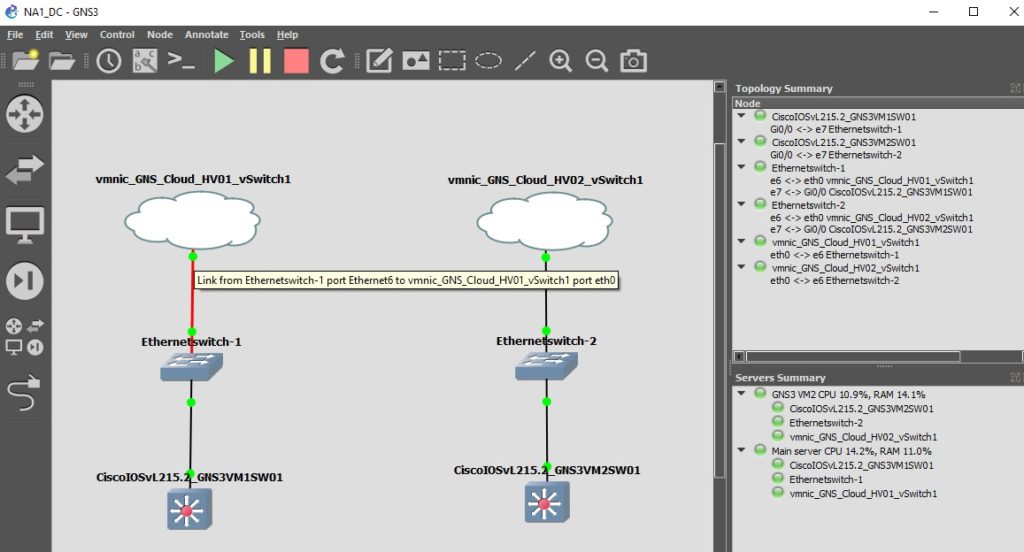
Issues with promisiocus mode and Cisco IOSvL2 crashing
Notice that my topology has a GNS3 Ethernet Switch between the GNS3 Cloud and the IOSvL2 images? With promiscuous mode enabled and an interface on a Cisco IOSvL2 router connected to a GNS3 cloud, the Cisco IOSvL2 routers would crash fairly quickly with traceback errors. My home lab is a ‘fairly’ elaborate setup with dozens of vlans. It could be that with promiscuous mode enabled there is just too much BUM traffic causing the image to crash, I’m really not sure but it only took a few minutes before the image crashed.
To solve the crashing issue a GNS3 “Ethernet switch” was added between the IOSvL2 switches and the GNS3 Cloud. With the switch inline the IOSvL2 images no longer crash. I can only assume the GNS3 Ethernet switch is acting as a filter between the promiscuous enabled Cloud connection and the IOSvL2 images.
Advantages to using GNS3 VM’s on ESXi
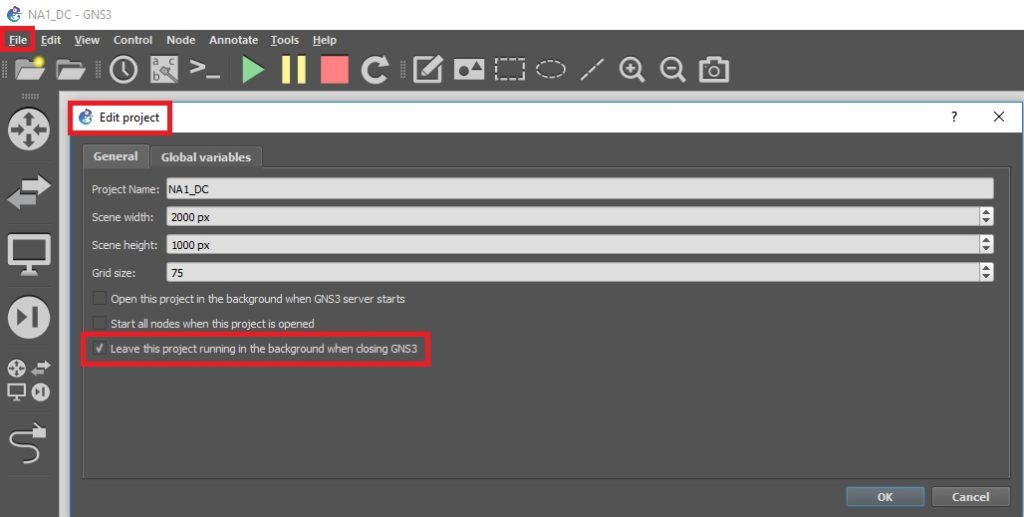
I’m currently running 2 GNS3 VM’s, one on each of my production hypervisors for capacity and use GNS3 in server mode. My projects can then be left running even after closing down the GNS3 GUI on my laptop. This is achieved by going into the settings for the Project and enabling:
“leave this project running in the background when closing gns3”
GNS3 scales pretty well with the multiple VM approach. You can even link devices together running on different VM’s, GNS3 uses UDP tunnelling to achieve this so be sure the VM’s can communicate with each other if they reside on different networks.
Summary
I’m glad I put the effort in to switching to running the GNS3 VM’s on my ESXi servers. I can now build bigger, more elaborate lab’s. I also love the fact I can leave the lab’s up and running even after closing down the GNS3 GUI on my laptop.
Want to know why my vSphere Web GUI is that cool dark themed colour? Its a chrome extension you get from here 🙂

